This guide looks at adding a proxied Cloudflare service to a server set up with RunCloud and fail2ban with a WordPress jail conf set up.
Once you start using Cloudflare as a CDN solution for your hosting, you are adding another firewall into the equation, albeit a very good one, but you may want to pass your servers local firewall fail2bans IP blocks over to Cloudflare and keep the two firewalls synchronised. This guide is using a RunCloud/fail2ban set up with Cloudflare as a proxy.
2 problems need to be overcome, the first is the transparency of Cloudflare’s IP addresses and the second is pushing the fail2ban IP bans on your server firewall over to the Cloudflare firewall.
Reveal Visitor True IP Addresses on NGINX and Cloudflare
Cloudflare wraps a visitors IP address in its own address, this can cause issues with the fail2ban IP rules as you may be blocking the wrong addresses, so the real IPs need to be revealed – this is referenced on the Cloudflare site, and has a number of solutions for different web serving apps.
Runcloud uses nginx as a webserver and this extra config for Cloudflare is available in an addon to their default nginx config: wpbeaches.location.main-before.cloudflare-realip.conf
# CloudFlare proxy addresses. set_real_ip_from 103.21.244.0/22; set_real_ip_from 103.22.200.0/22; set_real_ip_from 103.31.4.0/22; set_real_ip_from 104.16.0.0/12; set_real_ip_from 108.162.192.0/18; set_real_ip_from 131.0.72.0/22; set_real_ip_from 141.101.64.0/18; set_real_ip_from 162.158.0.0/15; set_real_ip_from 172.64.0.0/13; set_real_ip_from 173.245.48.0/20; set_real_ip_from 188.114.96.0/20; set_real_ip_from 190.93.240.0/20; set_real_ip_from 197.234.240.0/22; set_real_ip_from 198.41.128.0/17; set_real_ip_from 199.27.128.0/21; set_real_ip_from 2400:cb00::/32; set_real_ip_from 2606:4700::/32; set_real_ip_from 2803:f800::/32; set_real_ip_from 2405:b500::/32; set_real_ip_from 2405:8100::/32; set_real_ip_from 2c0f:f248::/32; set_real_ip_from 2a06:98c0::/29; real_ip_header X-Forwarded-For;
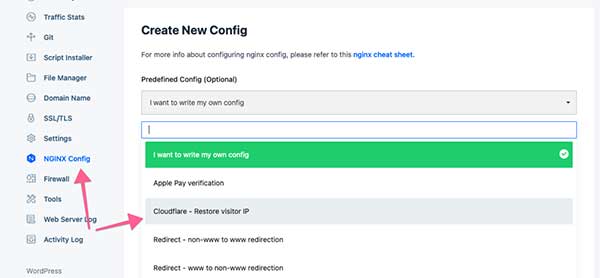
So login to your RunCloud panel and app and select nginx config > Create Config and choose the Cloudflare one from the list
Reveal Visitor True IP Addresses on Cloudflare and OpenLiteSpeed
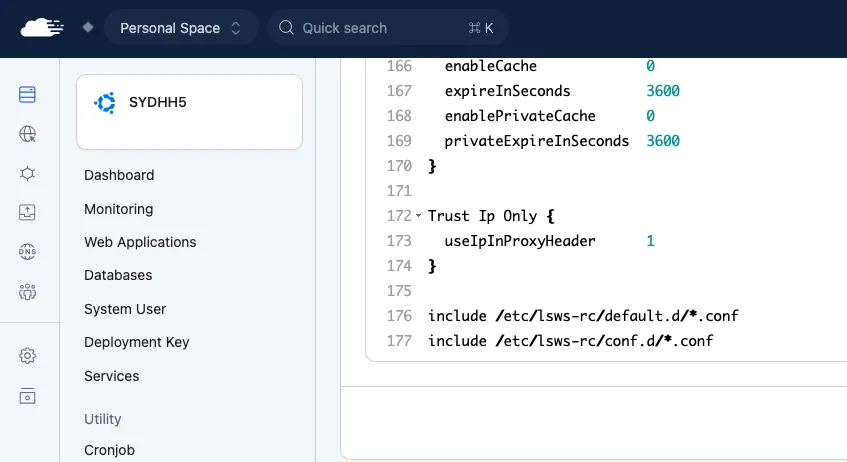
If you are using LiteSpeed instead of NGINX you need to add a Server configuration to your Open LiteSpeed config file:
Trust Ip Only {
useIpInProxyHeader 1
}
Pushing fail2ban IP rules to Cloudflare
For every fail2ban jail client you set up, as in the one set up for wordpress you can add an action when the fail2ban rule is triggered, there is a whole bunch of actions in /etc/fail2ban/action.d/ directory including a cloudflare.conf one, which synchronises your local firewall to the Cloudflare one.
The cloudflare.conf one supplied fails to work depending on the version, the one on github is updated and a better source, last updated Jan 2021.
The Cloudflare conf below is from version 0.11.2
https://github.com/fail2ban/fail2ban/blob/master/config/action.d/cloudflare.conf
You just rename/backup the old cloudflare.conf.original and add in the new one above best a new file name so it doesn’t get overwritten cloudflare.conf
Then add in your Cloudflare username/email and Global API key at the bottom where indicated on lines 81 & 83.
Then you reference the action in your jail.local file under the WordPress defined jail.
[wordpress]
enabled = true
filter = wordpress
logpath = /home/*/logs/nginx/*_access.log
maxretry = 3
port = http,https
action = cloudflare
iptables-allports
One of the differences here from the before configs which make it work is the indented iptables-allports
Restart fail2ban
service fail2ban restart
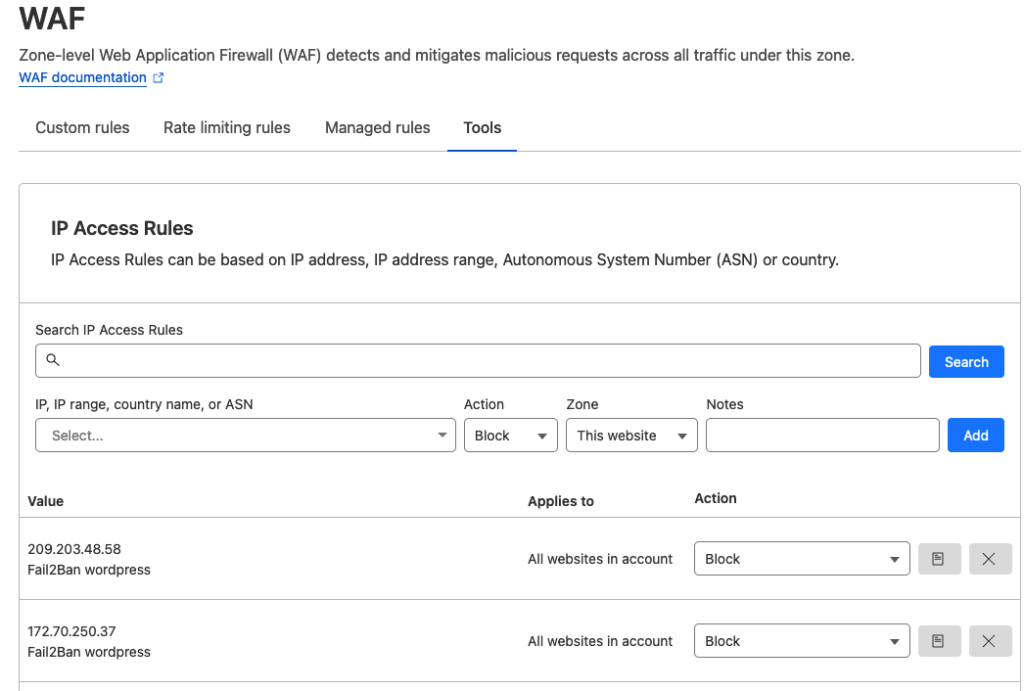
Now you will see your Cloudflare firewall updated with your RunClouds fail2ban banned IP addresses and if you unban addresses they will also be sync’ed.
So if you ban an IP address at your server firewall (example below uses our wordpress jail…
fail2ban-client set wordpress banip 1.2.3.4
It will be sync’ed to Cloudflare.
Then remove it from your local server firewall.
fail2ban-client set wordpress unbanip 1.2.3.4
And again it will be sync’ed to Cloudflare.