You can block the xmlrpc.php WordPress file when running on OpenLiteSpeed by adding a rewrite rule in the .htaccess file. This will reduce the brute force threat of bots making multiple resource requests.
Add to your webroot .htaccess file either add it in a mod_rewrite existing block or add a new one:
<IfModule mod_rewrite.c> RewriteRule xmlrpc - [F,L] </IfModule>
Then a server 403 error is returned when the file is requested.
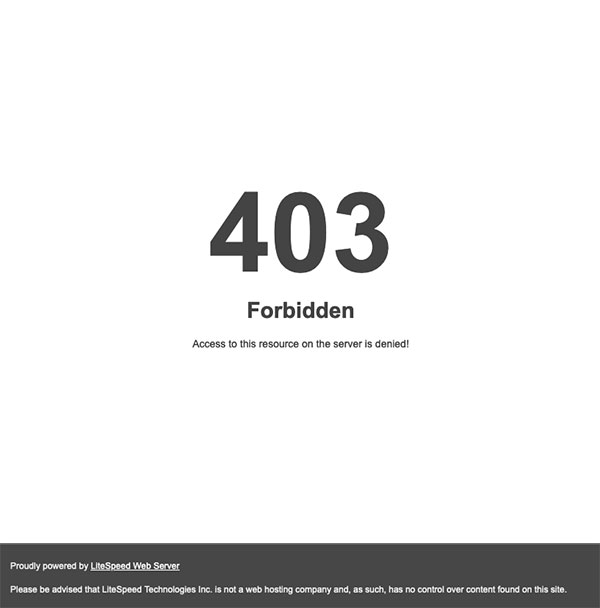
Or you can also block another WordPress file that gets a lot of hits, so 2 files: xmlrpc.php and wp-trackback.php, like so:
<IfModule mod_rewrite.c> RewriteRule ^(xmlrpc\.php|wp-trackback\.php) - [F,L] </IfModule>
If you wanted to exempt a particular IP address you can use:
<IfModule mod_rewrite.c>
RewriteCond %{REMOTE_ADDR} !^123\.456\.78\.910
RewriteRule xmlrpc - [F,L]
</IfModule>
If you wanted to exempt JetPacks CIDR notation IP addresses, you can use:
<IfModule mod_rewrite.c> RewriteCond expr "! -R '122.248.245.244/32'" RewriteCond expr "! -R '54.217.201.243/32'" RewriteCond expr "! -R '54.232.116.4/32'" RewriteCond expr "! -R '192.0.80.0/20'" RewriteCond expr "! -R '192.0.96.0/20'" RewriteCond expr "! -R '192.0.112.0/20'" RewriteCond expr "! -R '195.234.108.0/22'" RewriteRule xmlrpc - [F,L] </IfModule>
That’s it, this will save a lot of brute force attacks by dealing with unwanted requests at the OpenLiteSpeed server level.









2 comments
Cj
Brilliant thanks, works well
Tycoon
Does that mean the site can’t be attacked with xmlrpc blocked??? I don’t understand.