If you are using Cloudflare’s proxied traffic, you can block WordPress xmlrpc.php requests from Cloudflare by creating a Custom or Rate Limiting Rule for which on a free account you get one Rate Limiting Rule and 5 Custom Rules, attacks on xmlrpc.php are frequent and it is best now disabled as it will be deprecated from WordPress in the future, but unknown when at this stage.
Some of the more popular WordPress plugins such as JetPack still need to access xmlrpc.php so you may need a custom solution to make it available to certain IP addresses.
Remove xmlrpc requests with Cloudflare using Rate Limiting Rule
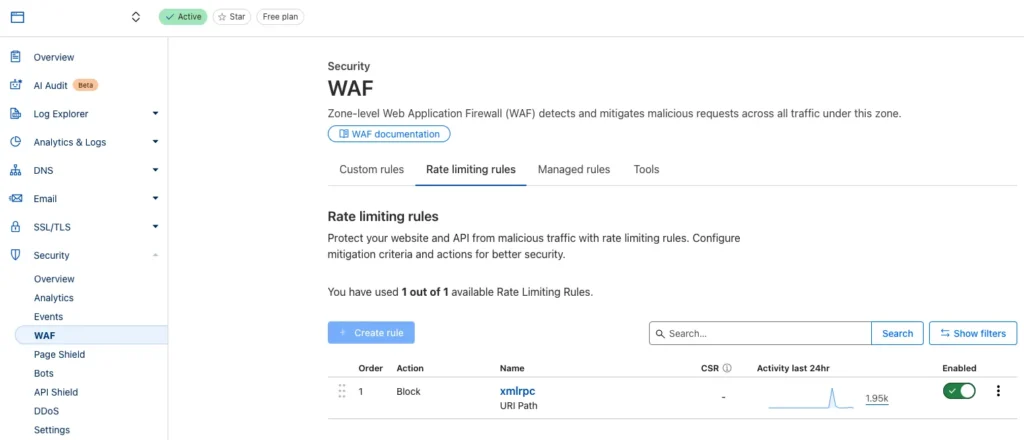
Find it under Security > WAF > Rate limiting rules
Create the rule as below…
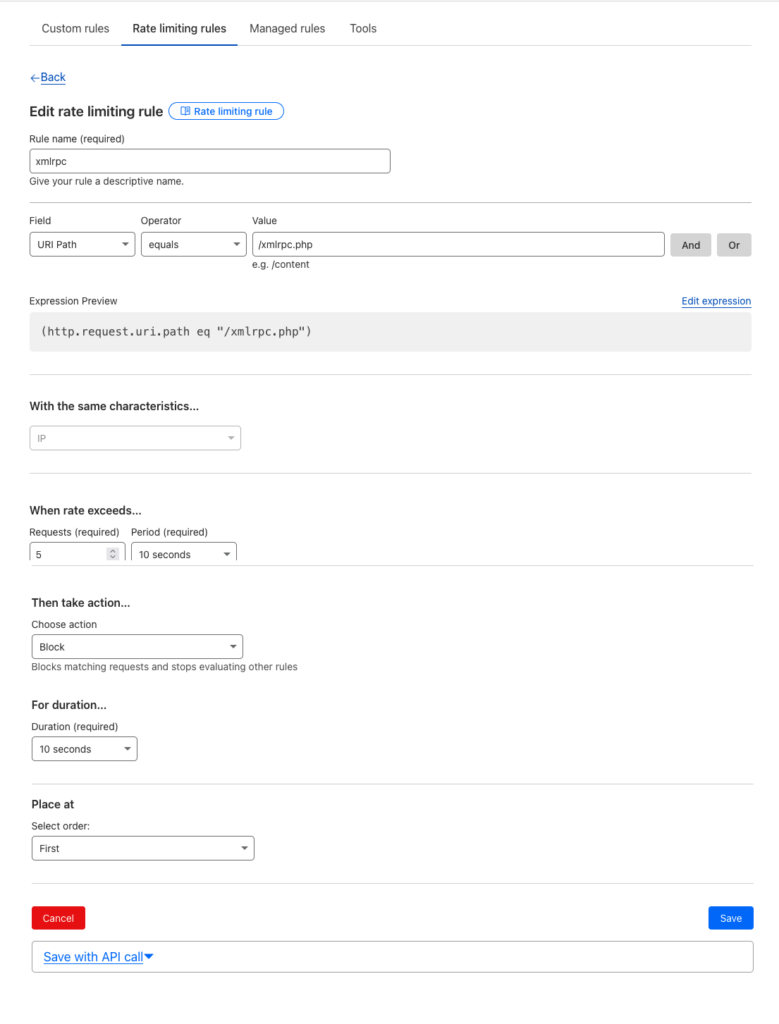
Use Cloudflares Custom Rules
You can also use Cloudflares Custom Rules, this can come in handy when you need to allow some IP addresses to request XMLRPC but not others such as the JetPack plugin.
Find it under Security > WAF > Custom Rules
Create the rule as below…
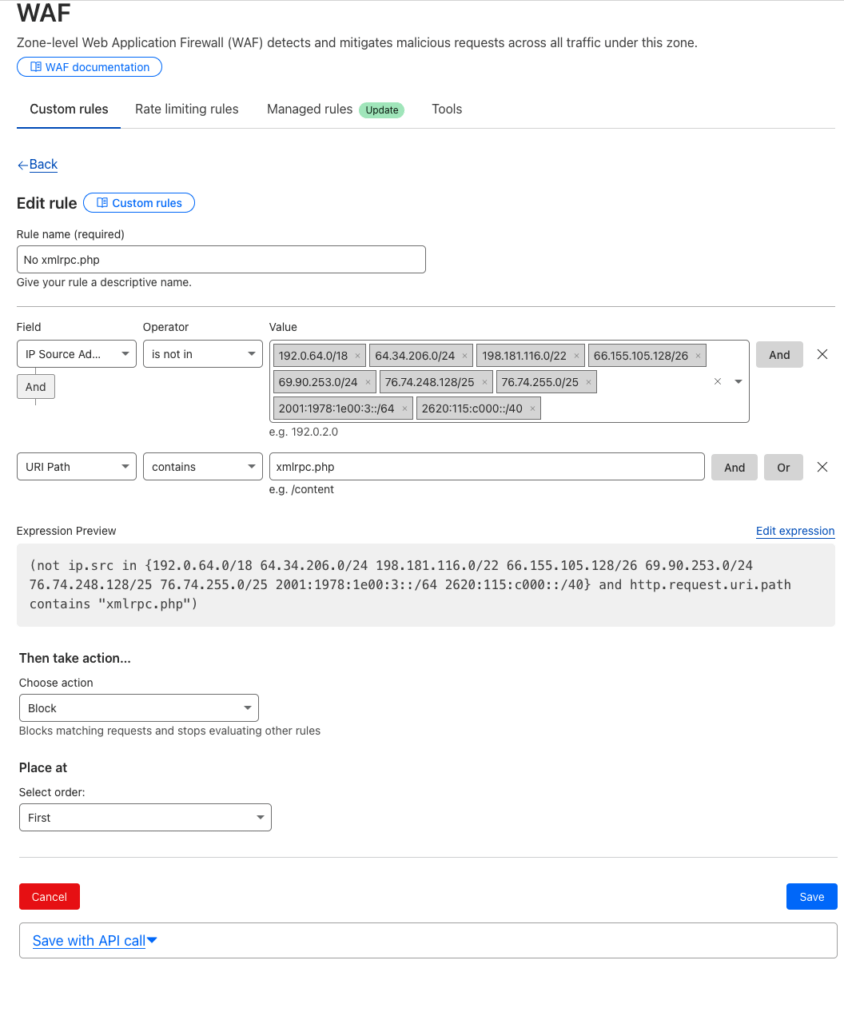
So in the above all IPs are blocked apart from Jet Packs IP addresses
JetPack IP Address Range
The JetPack IP address range is discussed on Github, published at JetPack, but is subject to change which can be verified here, and converted to CIDR notation here.
Disable xmlrpc.php via php filter or htaccess
Other ways to block xmlrpc.php can be donw with plugins such as Disable XML-RPC or a line of code in your functions.php
add_filter( 'xmlrpc_enabled', '__return_false' );
Or htaccess:
# Block WordPress xmlrpc.php requests
<Files xmlrpc.php>
Order Deny,Allow
Deny from all
</Files>
Check that xmlrpc is disabled with this online validator.









4 comments
Jeffrey Goh
Thanks for this. Most helpful as I was getting bombarded by calls to xmlrpc.php – not enough to cause a real problem, but enough to fill my nginx logs with crud.
Couple of updates :
1. https://www.cidrcalculator.com/ points to domain for sale (looks dodgy, may have been taken over). Use https://account.arin.net/public/cidrCalculator instead
2. Not sure JetPack keeps their list up to date (so in an abundance of caution, I started with the list in https://github.com/Automattic/jetpack/issues/1719#issuecomment-374788523 and included 87.250.160.0/19 as per http://whois.arin.net/rest/org/AUTOM-93/nets mentioned above.
Ahmed
Came across this article and would like to say Thank you!
I have a challenge rule for my xmlrpc.php causing jetpack not to work regardless to what cloudflare WAF jetpack is.
To allow jetpack, I had to whitelist jetpack server AS number by adding “AS2635” in the IP address column.
That did the trick for me.
user5555
Cloudflare actually has built-in Jetpack protection: https://support.cloudflare.com/hc/en-us/articles/218377098-WordPress-Jetpack-and-Cloudflare
“The Cloudflare WordPress WAF rule WP0007 protects xmlrpc.php file ion all Cloudflare plans to allow only Jetpack to use the xmlrpc.php?for=jetpack query string. Cloudflare does this by only allowing the IP range of Jetpack’s automation systems. As such any attempt to access xmlrpc.php?for=jetpack from an IP that is not a genuine Jetpack IP will be blocked with a HTTP 403 Forbidden message from Cloudflare. This in itself is nothing to worry about and improves the security of your website and does not affect the functionality of Jetpack whatsoever.”
Leonidas
Thank you for this.
Cloudflare now has an expression editor, so it looks like this (simply copy and paste):
(not ip.src in {122.248.245.244/32 54.217.201.243/32 54.232.116.4/32 192.0.80.0/20 192.0.96.0/20 192.0.112.0/20 195.234.108.0/22 192.0.96.202/32 192.0.98.138/32 192.0.102.71/32 192.0.102.95/32} and http.request.uri.path contains “xmlrpc.php”)