Dealing with brute force attacks on WordPress is an issue that you would need to address, this guide looks at adding a solution for WordPress sites running on ServerPilot on a Vultr instance but can be also used on platforms from other providers such as Digital Ocean.
Using fail2ban as a solution to brute force attacks works well, it is a server/client set up once the server side of fail2ban is established you then add the clients in the form of jails which are configured in fail2bans jail.local config file.
For WordPress the client set up can easily be added in the form of a plugin – WP fail2ban, you simply install and activate the plugin no plugin settings are required but you do need to copy or add a couple of filter files to your fail2ban filter directory on your server.
Copy both wordpress-hard.conf and wordpress-soft.conf from the WP fail2ban plugins filters.d folder to your /etc/fail2ban/filter.d/ server directory. The plugin author suggests to use both filters, I think that use both if you have an environment where multiple users are logging in or if it is a single user site use the wordpress-hard.conf filter.
With the filters in place now it’s time to add the config to the jail.local file.
[wordpress-hard] enabled = true filter = wordpress-hard logpath = /var/log/auth.log maxretry = 3 port = http,https
So above I am just using the harder filter if you want both filters just repeat the block and change the filter name.
Restart fail2ban
service fail2ban restart
Check the client is running
fail2ban-client status wordpress-hard
After a while you will see some failed attempts…
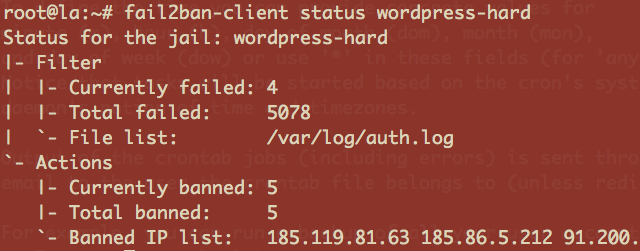
For successful and failed WordPress login attempts you can see these in the /var/log/auth.log log file. When the fail2ban filter is triggered and an action taken see the /var/log/fail2ban.log log.
Removing a banned IP address
To reinstate a banned address use the format below, the jail used here is the wordpress_hard jail.
fail2ban-client set wordpress-hard unbanip 1.2.3.4
Check out the plugin page for more options and additional logging.